What is SSL inspection in network security?

When you visit a website and see the padlock icon in your browser, it means your connection is encrypted through HTTPS. This encryption protects your data from outsiders, but it also hides the contents of that traffic from network security tools.
That’s where Secure Sockets Layer (SSL) inspection comes in. It’s a security technique that allows organizations to temporarily decrypt and scan encrypted traffic for threats before re-encrypting it and sending it to its destination. While this helps detect hidden risks and enforce security policies, it can also raise privacy and legal concerns.
In this article, we’ll explain how SSL inspection works, why organizations use it, and what its benefits and drawbacks are for users.
What is SSL inspection?
Secure Sockets Layer (SSL) inspection, also called Transport Layer Security (TLS) interception or HTTPS interception, is a network security practice that lets organizations see what’s happening inside encrypted traffic.
Most websites today use HTTPS encryption to keep data private, but that same encryption can also hide malware, phishing links, or data leaks. SSL inspection restores visibility into this traffic so threats can be detected before they reach users.
It’s commonly used in corporate and educational networks to protect against hidden attacks, enforce browsing policies, and meet compliance requirements. However, because it involves decrypting HTTPS connections, it must be implemented transparently and with safeguards to protect user privacy.
Learn more: Read our detailed explainer on SSL vs. TLS.
How does SSL inspection work?
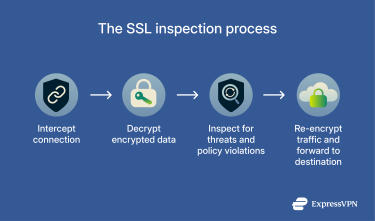 SSL inspection happens in real time and is usually invisible to end users. It can be applied to both outbound traffic (users visiting external websites) and inbound traffic (visitors accessing an organization’s secure services). In both cases, the goal is to uncover hidden threats within encrypted communications while maintaining overall data confidentiality and integrity. Here's the step-by-step process for how SSL inspection works:
SSL inspection happens in real time and is usually invisible to end users. It can be applied to both outbound traffic (users visiting external websites) and inbound traffic (visitors accessing an organization’s secure services). In both cases, the goal is to uncover hidden threats within encrypted communications while maintaining overall data confidentiality and integrity. Here's the step-by-step process for how SSL inspection works:
1. Interception
The inspection device (often a firewall, secure web gateway, or dedicated proxy) intercepts the HTTPS connection between a client and a website. It positions itself between the two endpoints, creating two encrypted tunnels: one between the client and the inspection system, and another between this system and the destination server.
2. Decryption
After interception, the inspection system doesn’t break SSL/TLS encryption; it relies on the way trust is established between certificates.
When a browser connects to a website via HTTPS, it receives the site’s certificate, which contains the public key used to encrypt data that only the website can decrypt with its private key. The authenticity of that certificate is verified through a chain of trust: each certificate is signed by the private key of a higher-level certificate authority (CA).
The browser verifies each signature using the corresponding CA’s public key until the chain ends with a root CA, whose public key is hardcoded in the operating system. Because the root CA’s key is built into the device, it can be inherently trusted, ensuring the certificate was legitimately issued for the domain you’re visiting. However, this does not guarantee the website itself is trustworthy, only that the certificate comes from a trusted authority.
An organization looking to perform SSL inspection adds its own CA certificate to the list of trusted root authorities on the device. When a HTTPS connection is established, the inspection system:
- Retrieves and holds the real certificate from the target website.
- Generates a new public/private key pair and creates a new certificate with identical details to the original website’s certificate.
- Signs this new certificate using its private CA key, producing a valid cryptographic signature.
- Sends the signed certificate to the user’s device, which accepts it as legitimate because it can verify the signature using the trusted CA public key installed earlier.
The device encrypts its traffic using the public key from this temporary certificate. The inspection system decrypts it using the matching private key it generated, allowing it to inspect the plaintext data.
3. Inspection
The plaintext data is passed to security tools for analysis. These tools check for malware signatures, phishing attempts, data leaks, or policy violations that would otherwise be hidden inside encrypted connections.
Depending on the network setup, the inspection process may involve other integrated controls, such as intrusion prevention or data loss prevention (DLP) systems.
4. Re-encryption
After inspection, the device re-encrypts the traffic using SSL/TLS before forwarding it to its destination. To handle responses from the website, the same full SSL inspection process is completed in reverse.
Benefits of SSL inspection
By providing a clear view into encrypted network traffic, organizations gain significant advantages in threat detection, regulatory compliance, and network visibility.
Enhanced threat detection and data protection
Encrypted traffic can conceal a wide range of cyberthreats, from viruses and phishing campaigns to command-and-control communications used by malware like Zbot.
SSL inspection exposes these hidden dangers by decrypting and scanning HTTPS traffic in real time, allowing security tools to block malicious websites, stop data-stealing scripts, and detect attacks disguised as legitimate connections. This reduces the overall attack surface.
Attackers also use encryption to smuggle stolen data out of networks undetected. SSL inspection helps identify these exfiltration attempts by revealing when confidential files or credentials are being sent to unauthorized destinations, allowing security teams to react quickly and prevent breaches before they cause serious damage.
Learn more: Check out our guide on what an SSL stripping attack is and how to prevent it.
Compliance with data protection regulations
Many industries must inspect encrypted traffic to comply with data-protection laws and financial oversight standards. SSL inspection lets organizations confirm that encrypted communications follow security and privacy policies while maintaining data integrity. It also demonstrates to auditors that encryption isn’t being used to hide violations or data leaks, helping companies avoid fines and meet compliance expectations.
User oversight and accountability
Beyond threat detection, SSL inspection provides visibility into user activity within encrypted channels. Security teams can see which sites employees access, which applications they use, and whether any risky behavior occurs.
This oversight helps identify insider threats, enforce acceptable-use policies, and support investigations during security incidents. It also improves accountability by giving organizations clear records of how encrypted resources are used across their network.
Risks and challenges of SSL inspection
While SSL inspection strengthens network defenses, it also introduces privacy, legal, and operational challenges. Organizations need to weigh these carefully and apply safeguards to prevent misuse or performance degradation.
Privacy concerns
Decrypting HTTPS traffic gives organizations deep visibility into user activity, which can lead to the exposure of sensitive personal data, such as emails, financial information, or health records. This raises legitimate privacy questions: what level of monitoring is acceptable, and who should have access to decrypted content?
Even if inspection is meant for security, it blurs the line between protection and surveillance. Employees might feel their personal browsing is being monitored, and users often have no clear way to tell what data is being inspected or who can see it. This loss of confidentiality is one of the most controversial aspects of SSL inspection and a major challenge for organizations that deploy it.
Performance and technical limitations
Decrypting, analyzing, and re-encrypting traffic consumes significant processing power. Each HTTPS session adds latency and increases CPU and memory use on inspection devices. If implemented without proper capacity planning, SSL inspection can slow down network performance and degrade user experience.
Organizations can mitigate this by deploying hardware acceleration, load balancing, or selective inspection (for example, excluding trusted sites such as banking or healthcare portals).
Learn more: You can read more about load balancing and traffic distribution in our reverse proxy guide.
Security and configuration risks
SSL inspection systems themselves can become weak points if not properly managed. Because they intercept and decrypt traffic, any compromise of the inspection device or its certificates could expose all network communications to attackers.
Poor configuration or outdated software may break legitimate connections, trigger browser warnings, or create loopholes that weaken encryption. Managing certificates adds another layer of risk. If a root certificate is mishandled, expired, or leaked, it can undermine trust across the entire network.
These issues make SSL inspection a double-edged sword: while it protects against hidden threats, it also introduces new ones if not carefully controlled.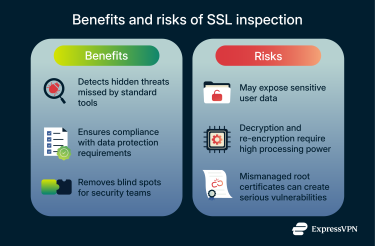
SSL inspection in VPN and network security
Virtual private network (VPN) connections add another layer of complexity to SSL inspection because they create encrypted tunnels that can get around network security controls.
Corporate VPNs connect different parts of an organization’s network through encrypted tunnels, and SSL inspection needs to work within this infrastructure to maintain security visibility. Organizations use VPNs for remote access, connecting branch offices, linking data centers, and giving third-party vendors access to corporate resources. Each scenario requires SSL inspection at different points in the network architecture.
The inspection happens at specific choke points where traffic flows through the corporate security infrastructure. Organizations deploy SSL inspection based on their network architecture and where users connect:
- On-premises deployments: For employees in the office, inspection appliances check all internet-bound traffic at the network edge.
- Remote workers and mobile employees: Organizations have two main options. They must either route all remote user traffic back through the corporate network for inspection, or use a cloud-based security gateway that inspects traffic between the remote user and the internet.
- Site-to-site VPNs: SSL inspection can occur at one end of the connection or at both ends. Organizations choose based on where they have the processing capacity and where threats are most likely to enter the network.
- Third-party vendor access: When vendors use a VPN to connect, their traffic should be directed through the same inspection controls to prevent breaches or data leaks.
Because the organization manages both VPN endpoints, it can deploy its own root certificate to decrypt traffic securely within those tunnels.
Personal VPNs, on the other hand, create device-to-provider tunnels that a network-edge inspection system can’t decrypt. Enterprises either block or rate-limit those tunnels or shift where inspection takes place so that traffic can be analyzed before the VPN encrypts it.
Learn more: Read our article that explains what VPN detection is and how it works.
How to implement SSL inspection successfully
Getting SSL inspection right requires careful planning and attention to technical, legal, and ethical considerations.
Choosing the right tools and technologies
Several technologies can perform SSL inspection, each suited to different organizational needs and network architectures. The right choice depends on your traffic volume, security requirements, and whether you prefer on-premises hardware or cloud-based services.
- Next-generation firewalls (NGFWs): These include SSL inspection capabilities, along with other security features such as intrusion prevention and application control. This option works well if you already have NGFW infrastructure in place.
- Dedicated SSL inspection appliances: High-performance devices can handle thousands of connections per second. Organizations with heavy traffic loads need these specialized appliances positioned throughout their network. They excel at offloading the decryption and re-encryption processing burden from other security tools.
- Secure web gateways: Cloud-based services combine SSL inspection with web filtering and cloud security. These route your traffic through cloud security systems that handle the decryption and inspection. This reduces hardware requirements on your network but means your traffic travels to the cloud provider's data center for inspection.
- Proxy servers: Traditional proxy solutions can perform SSL inspection by acting as a man in the middle between clients and servers. They offer flexibility due to their ability to route traffic to different security inspection devices and they also provide load-balancing capabilities.
When evaluating tools, look for systems that support network security standards, can handle your traffic volume without introducing unacceptable latency, and integrate with your existing security infrastructure. The system should generate detailed logs for security analysis and support certificate management.
Step-by-step configuration guide
Implementing SSL inspection follows a structured process:
- Choose your inspection hardware or software: Place the SSL inspection device within your network path. The device must be sufficiently powerful to manage the process without causing significant network lag.
- Define the inspection scope and rules: Configure the device to identify which traffic streams to inspect. You can target all traffic or limit inspection to specific IP addresses or ports.
- Manage and deploy certificates: The inspection tool requires access to the correct private keys and certificates to decrypt traffic. You must import these into the device. Your client devices (e.g., employee laptops) must be configured to trust the CA used by the inspection tool to avoid browser trust errors.
- Configure specific security policies: These policies dictate exactly how the inspection tool responds to different threat types. For instance, you can create a policy to automatically block all connections containing known malware signatures or to alert a security team when patterns matching data exfiltration are detected.
Best practices for smooth deployment
Getting SSL inspection right from the start saves time and prevents disruptions to your network. Follow these practices to reduce user friction and maintain effective security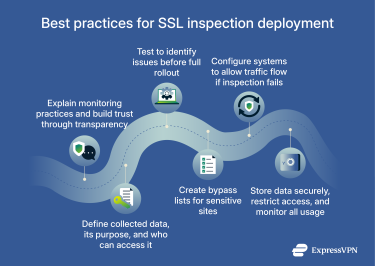
- Communicate with users: Let them know that encrypted traffic will be monitored and explain why before implementing SSL inspection. Transparency builds trust and reduces resistance to the change. Organizations often need to revise computer use policies and distribute them to all employees, contractors, and visitors who use the network.
- Create clear policies: Define what data will be collected, how it will be used, and who can access it. Make sure these policies comply with applicable privacy laws. Document your goals and work with stakeholders to define what traffic needs inspection.
- Start with gradual deployment: Begin with a limited group of users from various departments before rolling out to everyone. This lets you gain experience and catch problems early with minimal disruption. Test with a small percentage of traffic first.
- Exempt sensitive traffic: Financial sites, healthcare portals, and password managers often use certificate pinning, which breaks SSL inspection. Exempting these sites improves user experience without significantly reducing security. Build bypass lists based on web categories, destination addresses, or server names.
- Build in redundancy: SSL inspection failures shouldn't take down your network. Have a backup inspection system or configure your network to fail open (allow traffic without inspection) rather than fail closed (block all traffic).
- Protect your root certificate: Store it securely, limit access to it, and monitor for any unauthorized use. This certificate is as sensitive as any other critical security credential.
Legal and compliance considerations
SSL inspection sits at the intersection of security and privacy, creating legal obligations that vary by jurisdiction.
Regulatory frameworks affecting SSL inspection
Different regulations apply depending on where data is processed, the location of your network’s users, and industry. The General Data Protection Regulation (GDPR) restricts the collection and processing of the personal data of users in the EU, for example. SSL inspection can expose personal data, so organizations must have a legal basis for monitoring and inform users.
Under U.S. regulations, different laws apply to different sectors. Healthcare organizations must comply with the Health Insurance Portability and Accountability Act (HIPAA) rules to protect patient information. Financial institutions must follow regulations that require monitoring for fraud and money laundering while also protecting customer privacy. Government contractors must follow various security requirements that often mandate SSL inspection.
Employee monitoring laws differ by state and country. Some jurisdictions require explicit consent before monitoring employee communications. Others allow monitoring on employer-provided devices without consent but require notice. A few jurisdictions prohibit certain types of monitoring entirely.
Organizations that operate internationally must follow the most restrictive laws that apply to them. A company with offices in Europe and the U.S. must comply with GDPR even for its U.S. operations if it processes data about data subjects in the EU.
Balancing security and user privacy
Finding the right balance between security and privacy means making thoughtful decisions about what to inspect and how to use the data collected. Organizations need clear practices that protect both their networks and their users.
- Limit access to inspection logs: Not everyone needs to see detailed browsing histories. Security analysts might need access to detect threats, but that data shouldn't be available to managers for general employee monitoring. Strictly limit who can access decrypted data and digitally sign logs to ensure integrity.
- Set data retention policies: Keep logs long enough to investigate security incidents, but delete them after a reasonable period. This reduces damage if the logs are breached and limits the amount of historical data available for analysis.
- Use selective inspection when possible: Limit inspection only to high-risk traffic to reduce visibility into employee activities. Focus on unknown sites, questionable categories, or high-risk destinations rather than decrypting everything.
Organizations that implement these practices can maintain strong security without creating an environment where employees feel their every action is being watched.
FAQ: Common questions about SSL inspection
What does SSL stand for?
SSL stands for Secure Sockets Layer. It's an older encryption protocol that Transport Layer Security (TLS) has largely replaced. People still use the term "SSL" to refer to encrypted web connections, even though modern systems actually use TLS. When you see HTTPS in a web address, that's the secure version of HTTP that uses TLS encryption.
Is SSL inspection legal?
In many jurisdictions, Secure Sockets Layer (SSL) inspection can be legal if done in compliance with applicable laws and protections. The legality depends on factors such as device ownership, user notice, legitimate purpose, data protection laws, and jurisdictional rules.
How to inspect SSL traffic securely?
Protect the Secure Sockets Layer (SSL) inspection infrastructure at every level. Store the root certificate in a secure location, as unauthorized access could expose all decrypted traffic. Regularly update inspection systems with the latest security patches, restrict access to sensitive logs, and continuously monitor the inspection environment for signs of compromise.
What tools are available for SSL inspection?
Common Secure Sockets Layer (SSL) inspection tools include next-generation firewalls from vendors like Palo Alto Networks, Fortinet, and Check Point. Secure web gateways from companies like Zscaler and Cisco provide cloud-based SSL inspection.
Dedicated SSL inspection appliances from F5 and A10 Networks can handle high-volume traffic. On the other hand, open-source options like Squid proxy can perform basic SSL inspection. The right tool depends on your traffic volume, network architecture, and security requirements.
How can SSL inspection enhance cybersecurity?
Secure Sockets Layer (SSL) inspection improves cybersecurity by giving tools visibility into encrypted traffic, where threats often hide. It allows security systems to detect malware, block phishing, prevent data leaks, and stop command-and-control communication. Without it, encrypted traffic creates a significant blind spot, allowing attacks to operate undetected.
What should organizations consider before implementing SSL inspection?
Before implementing Secure Sockets Layer (SSL) inspection, consider legal requirements, network performance impact, and user privacy. Ensure you have capable hardware and skilled staff. Develop clear inspection policies, communicate them to users, and plan for certificate management. Define exemptions for sensitive traffic, like banking, and budget for ongoing maintenance costs.
Does SSL inspection work on VPN traffic?
Secure Sockets Layer (SSL) inspection can work on VPN traffic, though implementation can differ due to factors such as VPN type (remote access, site to site, commercial), where users are connecting from, and the overall network architecture.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN

















