Most secure operating systems in 2025 ranked: Secure data today

Staying safe online starts long before you open a browser tab. Your choice of operating system (OS) sets the baseline for everything that follows, from patch management and kernel hardening to the way apps handle your data. Pick the wrong platform, and even the best security habits won’t shield you from kernel-level exploits or silent telemetry.
This guide ranks today’s privacy-focused OSs, breaks down their security models, and shows where each one fits your threat model, whether you’re locking down a laptop, a mobile device, or a live-boot USB.
What makes an operating system secure?
Before diving into the rankings, we need a yardstick for measuring OS security. To earn high marks, an OS needs to do these things:
- Shrink the attack surface: Fewer exposed services mean fewer doors for intruders. Secure and privacy-friendly default configurations are a big plus, too.
- Keep workloads apart: Strong isolation stops a slip-up in one app from affecting the rest of the system.
- Frequent and automatic patches: Rapid fixes close new holes before they spread.
- Control access: Strong access controls ensure that only authorized users and processes can interact with specific resources. This involves verifying user identities, managing permissions meticulously, adhering to the principle of least privilege (PoLP), and implementing Mandatory Access Control (MAC) frameworks, such as SELinux or AppArmor.
- Protect data at rest and in use: Secure boot, disk encryption, and memory-safe code guard the bits you store and the processes you run.
- Ensures kernel integrity: The kernel, the very core of your OS, manages all system resources. A secure kernel minimizes potential entry points for malicious actors.
- Transparency and auditability: Whether an OS is open-source or closed-source impacts how its security is assessed and trusted. The most secure systems undergo regular independent security audits.
Privacy vs. security: What’s the difference?
Think of privacy and security as two sides of a door. Security is the lock blocking entry, while privacy is the frosted glass that prevents outsiders from seeing inside.
Security is about protecting your device and sensitive data from unauthorized access, disclosure, disruption, modification, or destruction. It relates to the integrity and availability of your information and systems.
Privacy centers on your right to control the collection, use, and sharing of your personal information. A secure OS might still collect and share lots of user data, thus impacting privacy. Conversely, a system can prioritize privacy but lack strong defenses against malware.
Our scorecard weighs both factors. A platform might beat all malware but still beam telemetry to third parties, or it might collect no personal data yet fall behind on patches. Ideally, you want both security and privacy.
Top secure operating systems ranked
We evaluated each OS using the criteria above, checked public vulnerability databases, and ran hands-on trials. This table shows our verdict at a glance:
| Rank | OS | Best for | Core strength | Trade-off |
| 1 | Qubes OS | Maximum security | Virtual machine (VM) compartments | Requires some initial learning |
| 2 | Tails OS | Ephemeral privacy | Live system that’s fully wiped after reboots | Limited persistent apps |
| 3 | Whonix | Anonymous browsing | Tor gateway + workstation split | Lower speeds through Tor |
| 4 | OpenBSD | Security-focused tasks, network infrastructure | Proactive security, integrated cryptography, code correctness, minimal/auditable codebase, secure by default | Lacks some desktop features/drivers/software, fewer packages, limited GUI, not for beginners, less convenience |
| 5 | Ubuntu | Everyday Linux | Fast, predictable patches | Telemetry disabled by default |
| 6 | macOS | Security with polish | Hardware/software integration | Closed-source core |
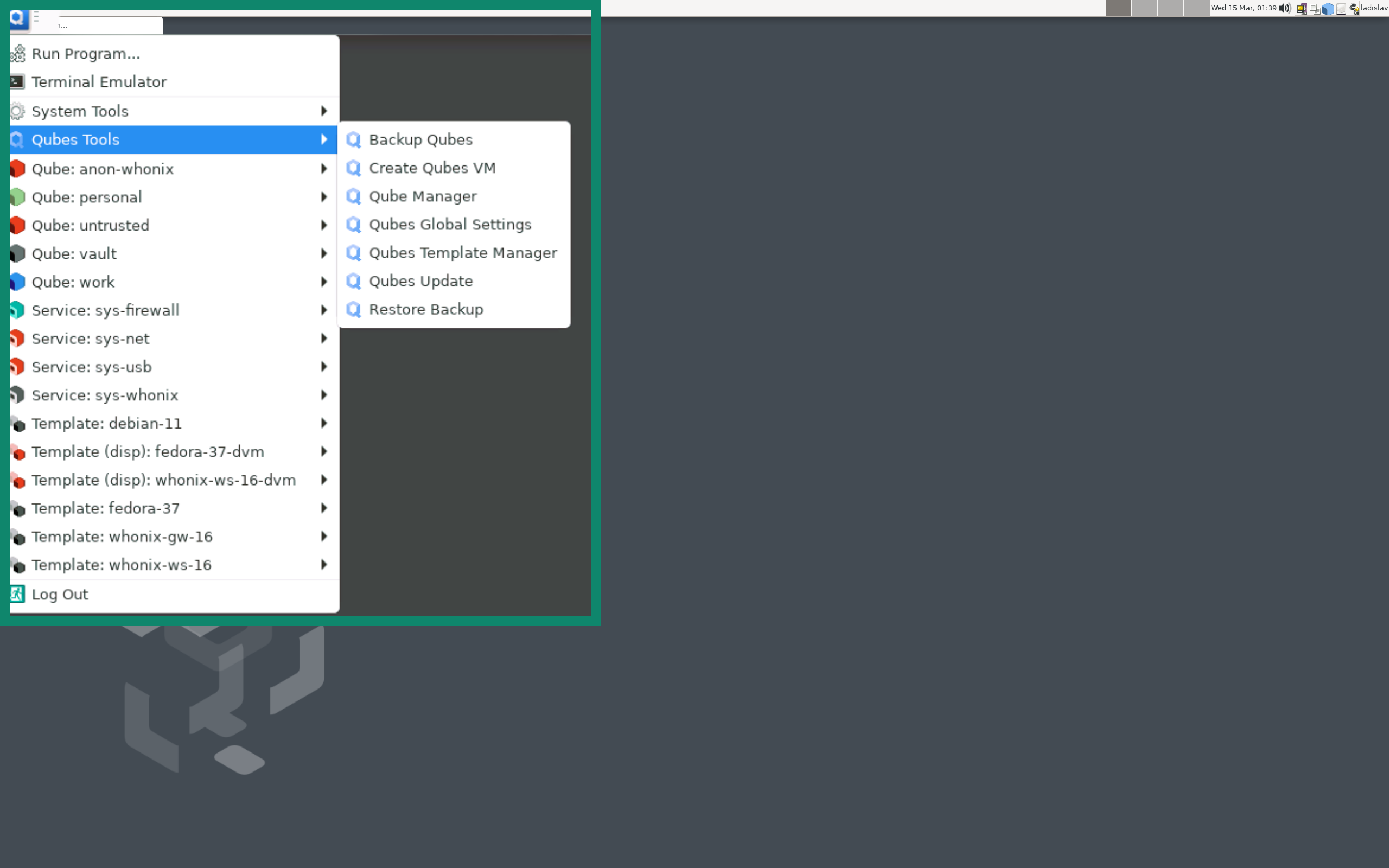
1. Qubes OS: Best for security
 OS type: Desktop Linux distribution
OS type: Desktop Linux distribution
Based on: Debian, Fedora
Architecture: x86_64
Desktop: Xfce with secure window borders
Qubes OS has a well-earned reputation as one of the most secure Linux distributions. A fully encrypted OS, it achieves security through compartmentalization. Every task, including email, web browsing, document editing, runs inside its own lightweight VM called a qube. This means that any malicious code exploiting, for example, your PDF viewer will be confined to that qube and disappear when the window closes.
Each qube draws its software from a read-only template. Update the template once, and every qube based on it inherits the fix. Keys stay in their own isolated “vault” qube; even the clipboard requires a deliberate copy command before data moves between compartments. Because the system leans on Xen rather than a full desktop hypervisor, you get all the benefits without most of the performance issues of traditional VMs.
It does take a while to learn the ropes (about a week, in my experience), but that’s to be expected. Install ExpressVPN inside your networking qube so that every domain and each qube’s traffic leaves the machine in an encrypted tunnel. (For Linux users comfortable with the command line, setting up ExpressVPN using its command-line interface (CLI) app within the networking qube can be streamlined. Read more about this in: How to set up and use the ExpressVPN CLI app for Linux.)
Key security features
- One patch refreshes all qubes built from that template.
- Each application runs in its own isolated VM using Xen Hypervisor.
- Color-coded window borders; an instant visual hint that signals trust level.
- Keys stay inside a minimal qube; apps never see them directly.
- A specialized, less privileged domain manages the graphical interface, further isolating it from application qubes.
- Shortcuts that move data between qubes require confirmation.
- Fine-grained control over network access for individual qubes, letting you specify which applications can connect to the internet.
Who should use it?
Pick Qubes when airtight separation matters more than quick setup. Expect to spend a week learning the ropes. Installing ExpressVPN inside the networking qube will encrypt every compartment’s traffic before it touches the physical adapter.
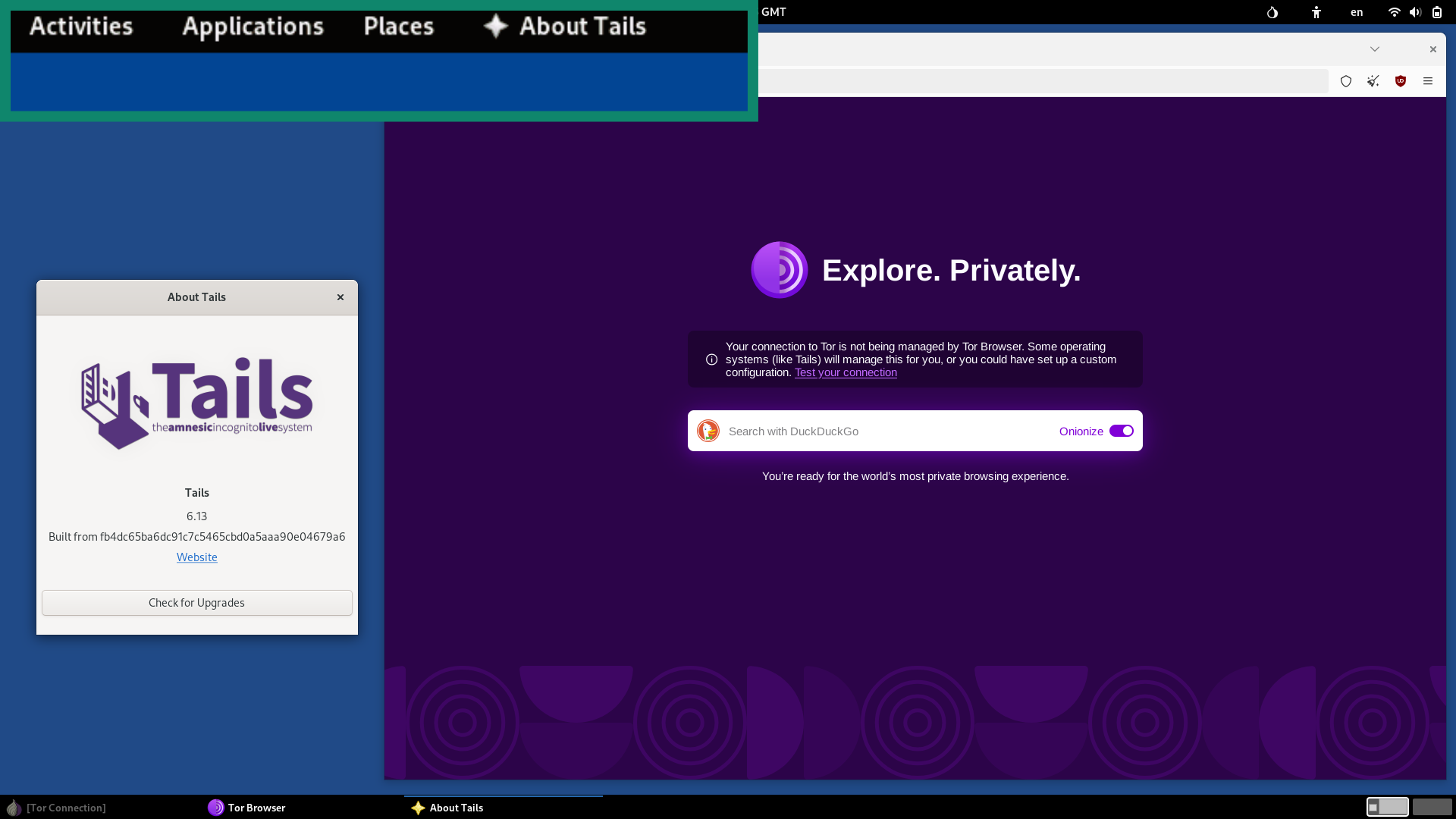
2. Tails OS: Best for privacy
 OS type: Live Linux (USB or DVD)
OS type: Live Linux (USB or DVD)
Based on: Debian
Architecture: x86_64
Desktop: GNOME with the Activities overview trimmed
While Qubes builds walls, Tails wipes the slate clean each time you shut it down, making it a privacy-focused OS. This Debian-based Linux distribution boots from a USB stick and routes every connection through Tor, leaving no trace on the host computer. Even the MAC address resets at startup, confusing network logs.
Because it never stores data on the internal drive, forensic recovery isn’t of much use. You can add an encrypted “persistent” partition for select files, but the rest of the system will still revert to a fresh state on every reboot.
The downside is that, due to the Tor integration, intensive browsing can feel sluggish.
Key privacy features
- Anonymizes internet traffic and thwarts fingerprinting with Tor.
- MAC spoofing at each boot confuses network logs.
- Optional encrypted storage lets you keep select files between sessions.
- Built‑in Electrum handles private Bitcoin payments.
📖Read more about other private browser options: Private browser: Your best options for online privacy.
Best use cases
Portable and stateless, Tails is ideal for use on hardware you can’t fully trust. The incorporation of Tor can hurt network speeds, though.
Tails excels at providing privacy, with a security model heavily reliant on its amnesic nature and the Tor network. If you’re looking for a primary OS with more surefire protection against sophisticated attacks, Qubes OS is probably better.
3. Whonix: Best for anonymous browsing
 OS type: Linux
OS type: Linux
Based on: Debian 12
Architecture: x86_64
Desktop: KDE Plasma or Xfce
Whonix divides your internet traffic between two separate VMs that sit atop your primary OS. This approach isolates your online activity for greater security and privacy.
Similar to Tails, Whonix is a great OS for anonymity thanks to Tor. While its dual-VM architecture adds a security layer by isolating applications from the network, it might not offer the same comprehensive security-by-compartmentalization against local threats as Qubes OS.
Tor integration and security
Whonix runs Tor in a small Gateway VM and everything else in a separate Workstation VM. The Workstation has one route, straight to the Gateway, while the Gateway’s firewall forces every packet into Tor and drops anything else. Any malware that escapes will only see Gateway’s private address.
Tor wraps traffic in three encrypted layers and bounces it through at least three relays, so no node links you to the site. Whonix gives each program its own Tor tunnel, shuts off little-used network routes that could leak your real IP, and bundles Tor’s newest upgrades Conflux for quicker connections and Arti (rewritten in the safer Rust code).
Who should use it?
Use Whonix when avoiding revealing your real location is paramount. That includes investigative reporters, whistle-blowers, political activists, security researchers, and anyone handling sensitive data.
Skip Whonix if you only need light privacy for casual browsing, if your computer can’t spare the extra memory for two VMs, or if you run high-bandwidth tasks like gaming or torrenting.
4. OpenBSD: Best for securing infrastructure
 OS type: Unix
OS type: Unix
Based on: NetBSD
Architecture: x86_64
Desktop: FVWM, GNOME, XFCE
OpenBSD is a security-focused Unix-based OS with integrated cryptography. It’s notable for an emphasis on code correctness, proactive security, and minimizing attack surfaces. Though mainly used on network infrastructure like servers, routers, and firewalls, OpenBSD can be deployed on desktops (though it isn’t really suitable for beginners).
Security and privacy are baked in, not bolted on. Unlike many OSs that add security features after core functionality is built, OpenBSD integrates them from the start into the kernel, system libraries, and userland tools.
What makes OpenBSD stand out?
Here’s what sets OpenBSD apart from other Unix-like systems:
- Default configurations maximize security: Limits unnecessary services out of the box and ships with strict access controls, reducing attack surface.
- Proactive security features: “Pledge” and “unveil” are mechanisms that limit programs’ capabilities and access to systems.
- Pledge and unveil: Unique system calls that limit what programs can do and what parts of the file system they can access.
- Minimal and auditable codebase: Streamlined base code free of frills (rigorously reviewed).
- Integrated cryptography: Tools such as OpenSSH ensure secure communication without needing third-party software.
What are the limitations?
Prioritizing security over convenience, OpenBSD lacks support for some modern desktop features, hardware drivers, and popular third-party software. Its strict development model means fewer packages and slower adoption of bleeding-edge tech. With only a limited GUI, expect to spend more time in the terminal.
5. Ubuntu: Best secure Linux for everyday use
 OS type: Linux
OS type: Linux
Based on: Debian
Architecture: armhf, ppc64el, riscv, s390x, x86_64
Desktop: GNOME, Unity
One of the most popular Linux distributions, Ubuntu is a common first stop for users migrating from Windows or macOS. It’s user-friendly and has a massive software repository and well-maintained security architecture. Canonical (Ubuntu’s publisher) has a dedicated security team that constantly audits and patches vulnerabilities.
Every long-term support release of Ubuntu guarantees 5 years of security updates (with an option to extend this to 10 years). This long support window and enterprise-grade maintenance make Ubuntu a safe, reliable choice for both everyday users and servers.
Security strengths and weaknesses
While not purpose-built for extreme security, Ubuntu is still a highly secure option. Here’s a quick look at its strengths and weaknesses.
Strengths:
- Long-term support (LTS) releases stay patched for 5 years; Ubuntu Pro stretches coverage to 10.
- Kernel Livepatch slips fixes into memory without a reboot, keeping servers and desktops online (premium feature).
- AppArmor loads on first boot and cages many core services such as CUPS, NetworkManager, Snap, and systemd-journald.
Weaknesses:
- Only apps with an AppArmor profile get that extra cage, leaving gaps for less popular programs.
- The 2-year LTS cycle freezes many libraries; newer kernel defenses often reach Fedora or Arch first.
- AppArmor rules are simpler than SELinux, so fine-tuned policies are harder to write.
Comparison with other Linux distros
Compared to other distributions, Ubuntu strikes a balance between security, ease of use, and software availability. Though comparatively lacking in security features, Ubuntu is more accessible for less technically inclined users than the likes of Fedora and openSUSE.
Minimalist distributions like Arch Linux provide a more customizable base but also require greater manual configuration, so Ubuntu offers a secure but more approachable Linux experience.
Who should use it?
Choose Ubuntu when you want long support, easy unattended security fixes, and AppArmor that works out of the box; pick Fedora for the newest defenses and SELinux depth; lean on Arch openSUSE MicroOS (an immutable OS focused on transactional updates and container workloads) if you prefer to assemble your own hardening stack or value an immutable root.
6. macOS: Best balance of security and usability
 OS type: Unix-like
OS type: Unix-like
Based on: BSD/Mach kernel
Architecture: Apple silicon (ARM64) and legacy Intel (x86-64)
Desktop: Aqua/Finder
Built-in security features
macOS, Apple’s proprietary OS for its Mac computers, has an intuitive user interface and many integrated security features. While not immune to malware and exploits, macOS offers a relatively secure environment for the average user. These mechanisms run quietly in the background, so you needn’t be a tech expert to benefit.
Here are a few:
- Gatekeeper and notarization: Blocks apps that Apple hasn’t checked or that were changed after signing, stopping many threats.
- System Integrity Protection (SIP): Locks key system files so even an admin account, or most malware, can’t tamper with them.
- XProtect: Lightweight antimalware engine that tackles most threats.
- FileVault 2: Allows you to easily encrypt your entire disk, keeping your data safe behind a password or recovery key.
- Secure enclave: Isolated system that stores Touch ID, Face ID, and encryption keys where apps can’t read them.
- Lockdown mode: An optional profile that turns off message previews, shared albums, and other high-risk features.
- Rapid security response: Delivers patches between major updates, integrating urgent fixes.
- App sandboxing and privacy prompts: Fences each app and asks before it can access the camera, microphone, or GPS.
Is macOS really secure?
Apple’s tight grip on both hardware and software makes macOS a strong OS in terms of cybersecurity. It has good encryption, kernel-level protections, and regular patches. Additions like Lockdown Mode (2022) and Rapid Security Response (2023) raise the bar again by shielding high-risk users and closing zero-day holes within hours.
macOS still needs you to install updates, vet downloads, and watch for social-engineering tricks; older Intel-based Macs miss some newer hardware defenses. Stay patched, limit unsigned apps, and use a VPN (or at least Apple’s iCloud Private Relay) to maximize your security while using macOS.
Privacy-focused operating system alternatives
While our top-ranked OSs prioritize both security and privacy, certain alternatives place a greater emphasis on user privacy or cater to specific use cases like mobile:
GrapheneOS: Best for mobile security
 OS type: Linux
OS type: Linux
Based on: Android
Architecture: aarch64
Desktop: Launcher
GrapheneOS is a secure phone OS built upon the Android Open Source Project (AOSP). Its design philosophy centers on hardening the OS against exploitation and minimizing data harvesting.
Privacy and security features include:
- Hardened kernel: Incorporates numerous security patches and enhancements beyond the standard AOSP kernel.
- Sandboxed Google Play: Lets you use Google Play services within a restricted sandbox, safeguarding user data.
- Advanced privacy controls: Among other things, it comes with network permission toggles for individual apps.
- No bloatware: A lack of pre-installed applications and services makes for a smaller attack surface and fewer privacy risks.
Pop!_OS: Linux alternative with strong security
 OS type: Linux
OS type: Linux
Based on: Ubuntu, Debian
Architecture: aarch64,
Desktop: COSMIC, GNOME
Pop!_OS is ideal for users who want top-notch security without sacrificing power or flexibility. It’s popular with IT professionals and software developers thanks to the inclusion of handy development tools. It also has a secure foundation stemming from its Ubuntu base, with features like full-disk encryption enabled by default during installation.
It’s also an excellent choice for those who value convenience in security; e.g., you want encryption but don’t want to think about it, or you want updates but on your schedule. For added privacy, you can use Pop as a base OS and run Qubes or Tails in a VM on top. Of course, using Pop with a VPN and Tor Browser is an option too.
What about Windows?
Windows is a good choice for many users; in fact, it’s the choice that the vast majority of computer users make. It’s easy to use, compatible with a huge array of software, and the latest version (Windows 11) has stronger security measures than ever before. Out of the box, Windows can detect most malware and even block a decent percentage of malicious websites.
That said, there are some issues when it comes to both privacy and security. For one, Windows collects lots of telemetry data by default, some of which cannot be fully disabled.
As the most widely used OS, Windows is also the most targeted by malicious actors, with zero-day vulnerabilities being regularly exploited. Updates are frequent, but they’re far too easy to ignore. Finally, a high degree of complexity and abundance of third-party software increase attack surface.
Final thoughts
Every OS on this list has a distinct approach to maximizing security and privacy. Qubes isolates, Tails forgets, Whonix cloaks, OpenBSD keeps things simple, Ubuntu patches quickly, and macOS marries strict controls with a user-friendly presentation. Each protects your data in different ways, making it hard to say which is the safest OS overall.
Whichever route you pick, combine it with strong passphrases, two-factor authentication (2FA), regular updates, and ExpressVPN’s tunnel to cut off packet sniffers in transit. Security is a journey; pick the OS that fits your threat model and keep fine-tuning.
FAQ: Common questions about the most secure operating systems
What operating system is the most secure?
Due to its security-by-compartmentalization architecture, Qubes OS is widely regarded as the most secure desktop operating system (OS). For short, high-risk sessions, Tails takes the crown. By isolating applications and system components into separate virtual machines (VMs), it greatly reduces the impact of security breaches.
Is Linux the most secure OS?
While Linux offers a strong foundation for security because it’s open-source and customizable, it’s not universally the most secure operating system (OS). The security level varies greatly between distributions. Some, like Qubes OS, Tails, and Whonix, are specifically designed for high security and privacy. The actual security depends on the distribution’s design, default configurations, update frequency, and, importantly, user practices. Therefore, while many secure OS options are Linux-based, not all Linux distributions are equally secure.
What is the most secure computer system in the world?
The most secure computer systems aren't available in stores (and they aren’t single systems either). Rather, the safest operating systems (OSs) are custom-built, usually by governments. Imagine a computer locked in a vault, not connected to the internet, with special software and super strict rules about who can use it. For everyday use, a fully patched Qubes OS laptop with hardware security modules and ExpressVPN for encrypted transport sets the bar.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN






















Comments
How do you feel Linux Mint compares to the other distros you mentioned?
Linux Mint is pretty great too! Mint is also based on Ubuntu and just like Pop!_OS, it has reporting through Ubuntu disabled by default. In terms of privacy and security, it's quite comparable to Ubuntu.
Happy New year to you all especially you Marcus. Having read your comments I would just like to ask "Does UBuntu and Signal work OK in the UK?"